Lan to Lan over ADSL (DRAFT)
Nicolas Crovatti
November 22, 2002
PPTP Client Lan to Lan over ADSL (DRAFT)Nicolas Crovatti November 22, 2002 Contents |
I wrote this document to add a specific case to the PPTP Client Routing HOWTO written by Linus McCabe. The purpose of this document is to help you to setup a LAN to LAN PPTP connection over an ADSL link.
Here is a small amount of requirements needed to understand this document:
The following diagram tends to display in a graphic way the fact that the VPN pptp link must pass trough the ADSL pptp link.
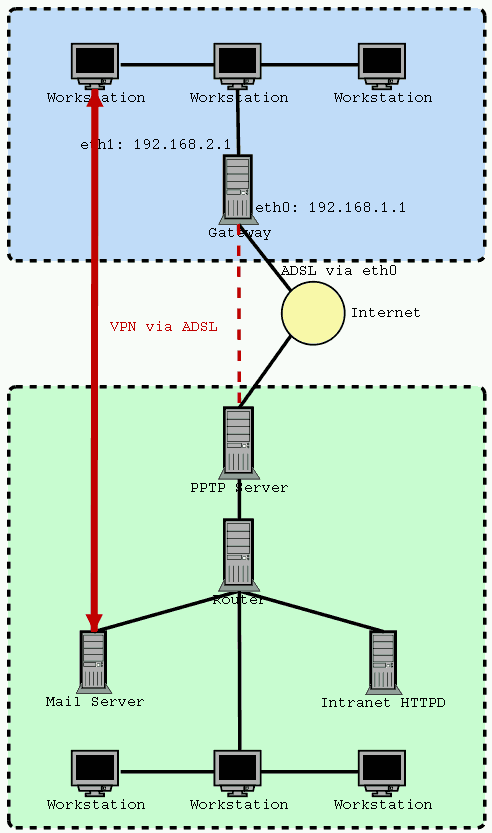
This section describes the Home network configuration.
A good thing to do before we start building firewall rules or adding new routes is to reference your VPN network IP class in your /etc/networks file.
This trick has two primary purposes:
For example:
# cat /etc/networks localnet 192.168.2.0 privatenet 10.0.0.0
To add an entry use this command as root:
# echo "privatenet 10.0.0.0" >> /etc/networks
In the same manner, if the foreign network doesn't provide a DNS server, you may want to use your /etc/hosts file to reference the commonly used IPs that are behind the VPN. But if available, you should prefer to add an entry to your /etc/resolv.conf:
# echo "nameserver 10.18.0.16" >> /etc/resolv.conf
When you are connecting to your VPN a new route will be automaticaly added to your kernel routing table. This is the route that will allow the connected box to reach the pptp server you are connected on. While connected with your ADSL your routing table may looks like this:
# route Kernel IP routing table Destination Gateway Genmask Flags Metric Ref Use Iface 193.253.1.1 * 255.255.255.255 UH 0 0 0 ppp0 localnet * 255.255.255.0 U 0 0 0 eth1 192.168.1.0 * 255.255.255.0 U 0 0 0 eth0 default 193.253.1.1 0.0.0.0 UG 0 0 0 ppp0
Where:
Start your VPN connection and then look again at your routing tables, you should have something like this:
# route Kernel IP routing table Destination Gateway Genmask Flags Metric Ref Use Iface 10.18.0.225 * 255.255.255.255 UH 0 0 0 ppp1 193.253.1.1 * 255.255.255.255 UH 0 0 0 ppp0 localnet * 255.255.255.0 U 0 0 0 eth1 192.168.1.0 * 255.255.255.0 U 0 0 0 eth0 default 193.253.1.1 0.0.0.0 UG 0 0 0 ppp0
As you can see, a new route as been created on ppp1 interface, this route is a Host route indicated by the H flag. In order to have our LAN computers able to use our VPN connection we must set a new route on the VPN's interface (ppp1) that leads to the foreign network.
To do this enter the following command as root:
# route add -net privatenet netmask 255.0.0.0 dev ppp1
The route you just added will allow you to reach other computers that are in the foreign network. Try it, grab the IP of your mail server and execute the following command:
# ping 10.18.17.94 PING 10.18.17.94 (10.18.17.94): 56 data bytes 64 bytes from 10.18.17.94: icmp_seq=1 ttl=125 time=326.3 ms 64 bytes from 10.18.17.94: icmp_seq=2 ttl=125 time=386.3 ms ...
If this works, then you're done. At least with routes...
The following commands are known functionnal, but you may have to customize them. these rules are adapted from the ones found in the pptp client routing howto. after rules customisation using a well referenced network, i added nat over the two involved ppp+ interfaces in order to avoid any netfilter infinite loops that happens while using nat on ppp1 only.
## Authorizing Outbound traffic from anywhere to foreign network # iptables --insert OUTPUT 1 --source 0.0.0.0/0.0.0.0 \ --destination privatenet/255.0.0.0 --jump ACCEPT \ --out-interface ppp0 ## Authorizing Inbound traffic from foreign network to anywhere # iptables --insert INPUT 1 --source privatenet/255.0.0.0 \ --destination 0.0.0.0/0.0.0.0 --jump ACCEPT --in-interface ppp0 # Authorizing packet forwarding from anywhere to the # foreign network using ppp0 interface # iptables --insert FORWARD 1 --source 0.0.0.0/0.0.0.0 \ --destination privatenet/255.0.0.0 --jump ACCEPT \ --out-interface ppp0 ## Authorizing packet forwarding from foreign network to anywhere # iptables --insert FORWARD 1 --source vpn_net/255.0.0.0 \ --destination 0.0.0.0/0.0.0.0 --jump ACCEPT ## Masquerading on ppp0 # iptables --table nat --append POSTROUTING \ --out-interface ppp0 --jump MASQUERADE ## Masquerading on ppp1 # iptables --table nat --append POSTROUTING \ --out-interface ppp1 --jump MASQUERADE ## Fixes the path MTU discovery problem # iptables --append FORWARD --protocol tcp \ --tcp-flags SYN,RST SYN --jump TCPMSS --clamp-mss-to-pmtu
This document was generated using the LaTeX2HTML translator Version 2K.1beta (1.48)
Copyright © 1993, 1994, 1995, 1996,
Nikos Drakos,
Computer Based Learning Unit, University of Leeds.
Copyright © 1997, 1998, 1999,
Ross Moore,
Mathematics Department, Macquarie University, Sydney.
The command line arguments were:
latex2html -antialias -split 0 tutorial.tex
The translation was initiated by Nicolas Crovatti on 2002-11-22
The diagram was produced using dia